As a business intelligence consultant, I have had the opportunity to deploy Power BI environments across multiple organizations operating within various industries. Throughout my experiences, I have understood that the invaluable nature of power BI lies in its ability to equip non technical-users with the proficiency to use data for insightful and effective decision-making. However, with this power comes the responsibility to safeguard sensitive information from unauthorized access or misuse – this is often a huge concern for management. In an era defined by growing data breaches and evolving governmental and company privacy regulations, the need for robust data protection measures and processes around your Power BI environment has never been more critical. From user authentication to efficient Power BI Apps and Workspaces, these best practices are always recommended to help you secure your data and maintain trust in your analytics.
User authentication
Microsoft Entra ID – the new Azure Active Directory (AD) – is the centralized directory and guardian of user identities in the Microsoft cloud. This cloud-based directory service has provided organizations with the ability to create user accounts and groups within Entra ID, enabling them to sign-in to various applications while using a single username and password within the Microsoft ecosystem, such as Power BI, Power Automate, Power Apps, Fabric, and more. It also handles licensing and permissions. Enforcing robust security policies like Multi-Factor Authentication (MFA) in Entra ID adds an extra layer of security, requiring additional forms of identification during sign-in, like texts or authentication apps. This adds an extra layer of protection against unauthorized access. Also, encouraging users to create strong passwords and enforce password policies such as minimum length, complexity requirements, and expiration periods enhances security not only in Power BI, but throughout all of your Microsoft ecosystem. Finally, with the location condition in Conditional Access in Entra ID, you can control access to Power BI based on the network location of a user. You can set up the location condition to block access from countries/regions where your organization knows traffic shouldn’t come from.
Tenant administration
Power BI provides several security features and capabilities within its admin panel to help administrators manage and secure their Power BI environment effectively. Security settings allow you to control who can publish reports, who can export, print and share content and whether users can self-register for Power BI – just to name a few. The admin panel also provides administrators access to usage metrics to see who went where and when. Detailed audit logs also track user activities and administrative actions. Administrators can review these logs to track user behavior, identify security incidents, and troubleshoot issues.
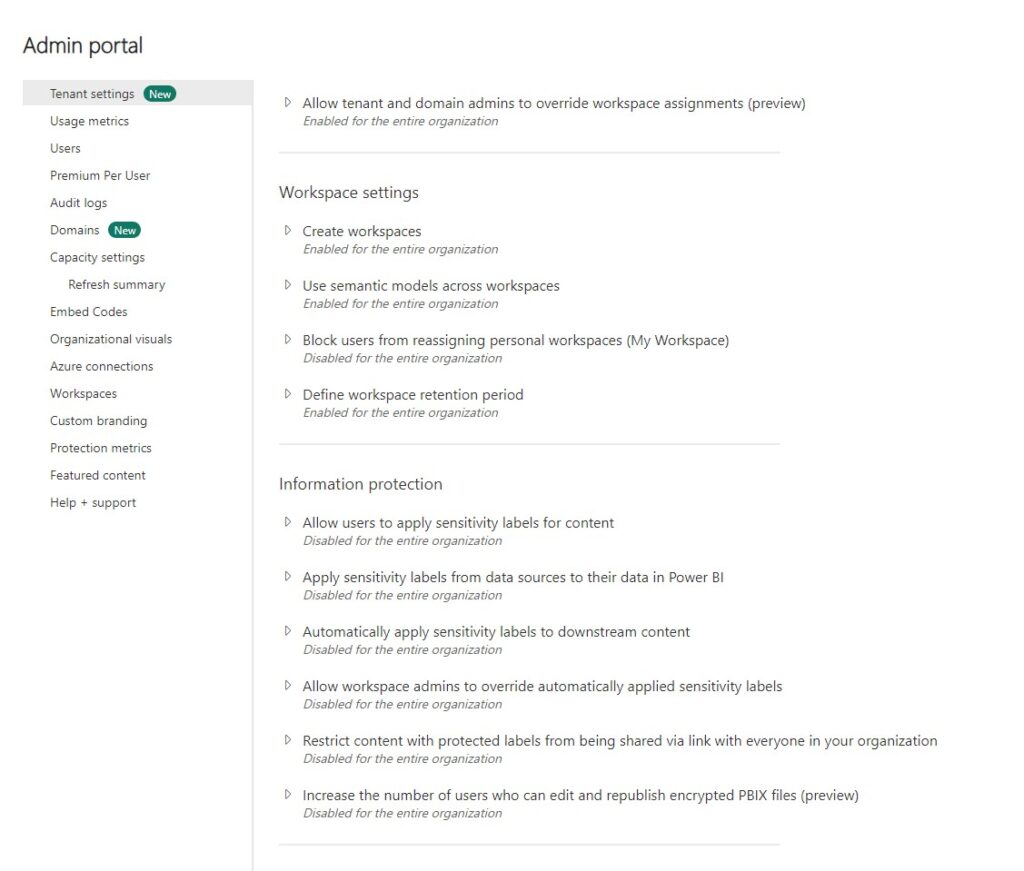
Group-Based Access
Previously, I exposed how robust security policies in the Power BI admin panel can help you secure your Power BI environment, protect sensitive data, and mitigate security risks. When you’re a medium or large organization and you’re allowing or preventing resources to access features that you can configure in the admin panel, the best practice is to use Entra ID groups that will be composed of users with common usage. Group-based access in Power BI allows you to manage access to content based on user groups rather than individual users. For example, you can create a level 1 group that will have access to everything and a level 2 group which will be limited to only certain features.
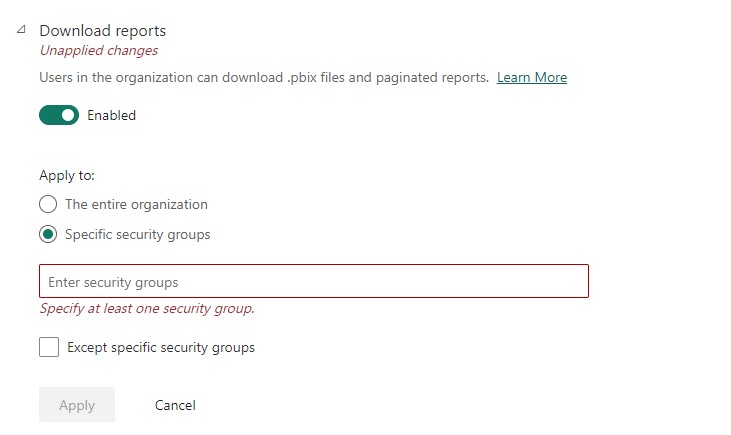
Groups can also be used when you set up row-level security and to give access to reports in apps and workspaces, which are two concepts that I’ll go explain in more detail later in this blog. One of the big benefits of using groups is the ability of granting access to multiple users of a group, instead of specific users. Any user who is a member of the group automatically inherits the associated permissions which can help you enforce security policies, manage on-boarding’s and departures more efficiently and also ensure that users only have access to the content relevant to their roles and responsibilities.
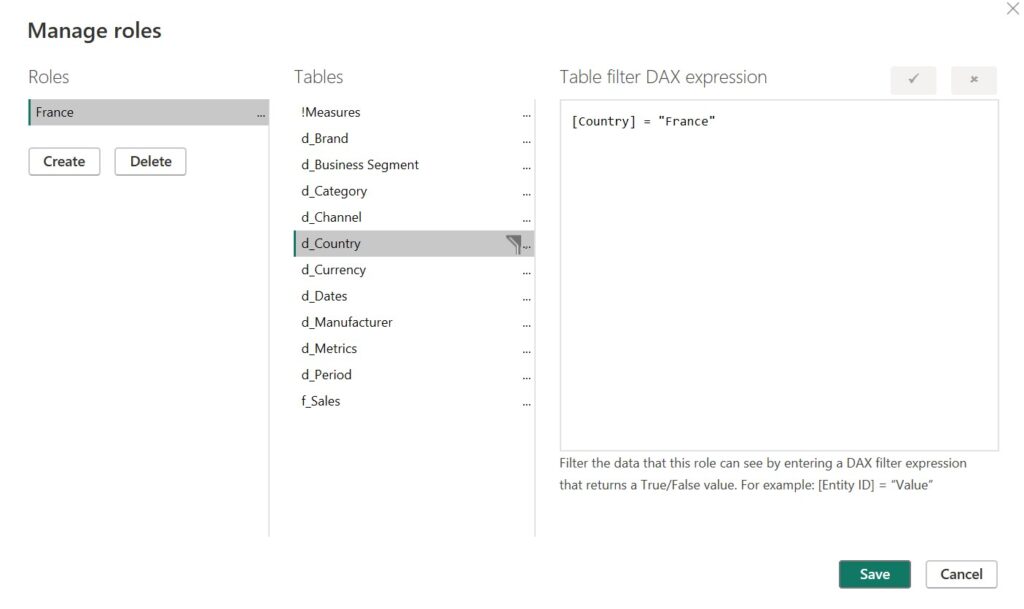
Row-Level Security (RLS)
Row-level security (RLS) in Power BI is a security feature that allows you to restrict access to data at the row level based on user or group roles and criteria’s. With RLS, you can ensure that users only see the subset of data that they are authorized to view, while other rows remain hidden from them. One of our clients with a presence in multiple countries asked us to implement RLS to make sure that users would only see data from their country. In their Power BI model, the RLS set up looked like this:
We can also set up RLS to be based on conditions, like this condition which restricts users to only see sales of under 1M$:
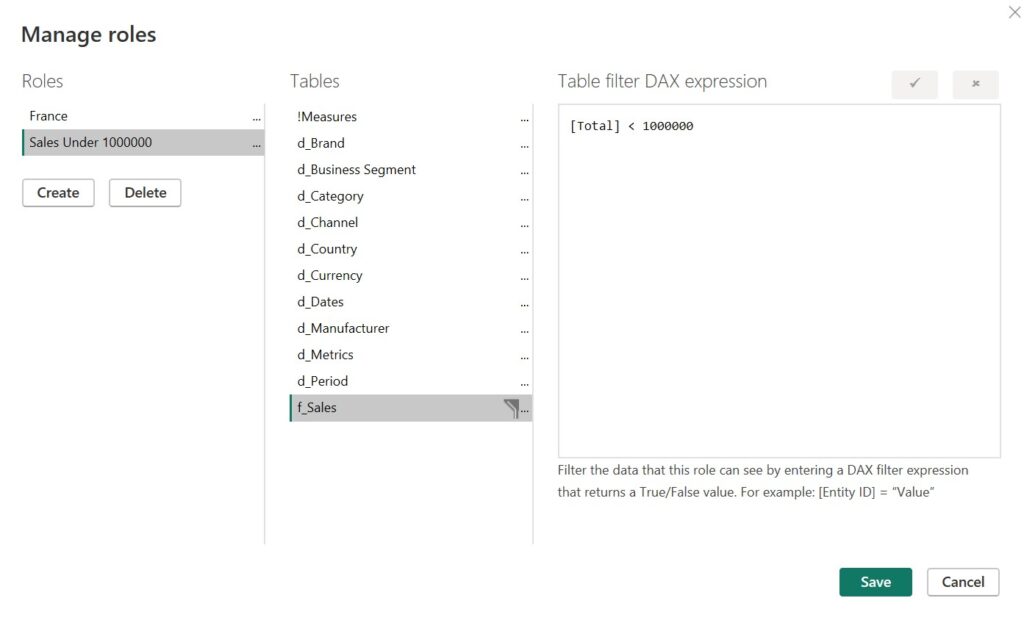
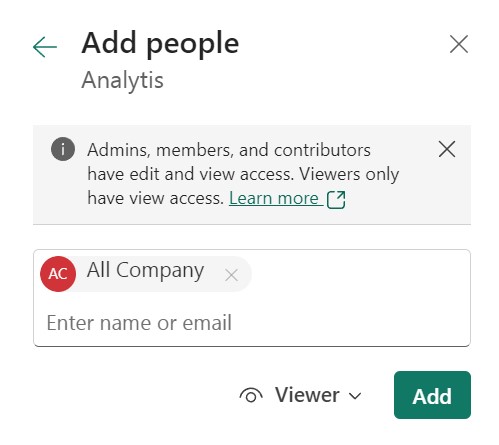
After you’ve created your roles and published your model in Power BI service, you need to add users that will be affected by the conditions or criteria’s of the role. As I’ve explained it in the group-based access section, you can use groups instead of individual users.
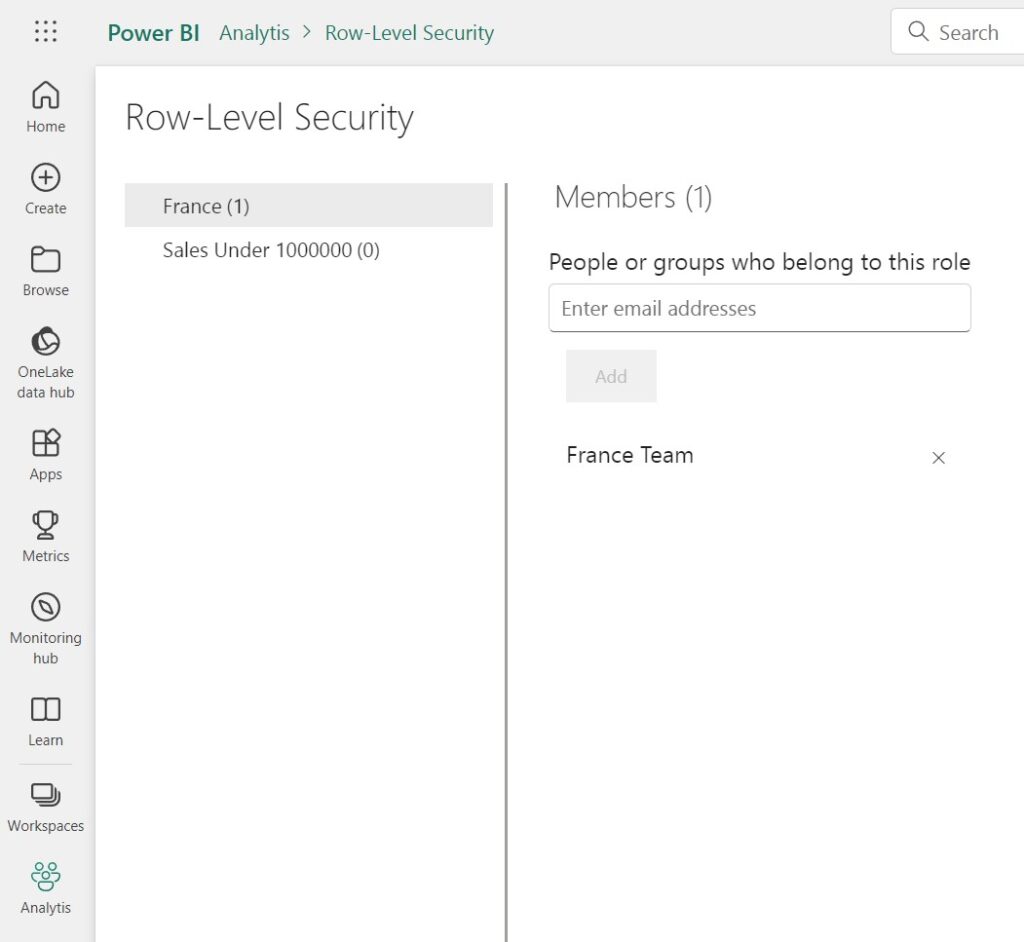
In a future blog post, I’ll explain how you can use the USERPRINCIPALNAME() function to dynamically assign a user e-mail from Entra ID to a RLS role.
Power BI Apps & Workspaces
Using Power BI apps and workspaces can significantly enhance security by isolating content and leveraging role-based access control. First, by segregating content into different app workspaces, you can logically separate data and reports based on business units, teams, or projects. This isolation ensures that users only have access to the specific content relevant to their roles, reducing the risk of unauthorized data exposure. On the other hand, role-based access control allow you to define granular permissions for different groups of users. You can assign roles such as Admin, Member, or Contributor to control who can view, edit, publish, or manage content within each workspace. This granular control ensures that users have the appropriate level of access based on their responsibilities. These roles and app permissions can be managed with Entra Id groups.




